• Home •
Victim΄s Story •
Fraud Prevention •
Project GSO •
Hall of Shame •
LINKS •

How Phishing works
What is phishing?
Phishing is a type of deception designed to steal your identity. In a phishing scam, a malicious person tries to get information like credit card numbers, passwords, account information, or other personal information from you by convincing you to give it to them under false pretenses. Phishing schemes usually come via spam e-mail or pop-up windows.
Phishing is a type of fraud that directs computer users to bogus websites. About two million users gave information to bogus websites resulting in direct losses of $1.2 billion for financial institutions and card issuers in 2003. Gartner Research (June 22, 2005) found that the number of phishing attack e-mail recipients grew 28% by mid-2005, based on a survey of 5,000 online U.S. consumers.
The Federal Trade Commission and the Anti-Phishing Working Group offer the following additional tips:
Use anti-virus software and a firewall, and keep them up to date. They can protect you from inadvertently accepting fraudulent files. Download free software patches if your browser offers them.
Never give personal or financial information in e-mail messages. E-mail isn't a secure method of transmitting personal information.
If you want to provide personal or financial information through an organization's website, look for a padlock icon on the browser's status bar (not in the content of the Web page), or a URL that begins "https."
Check all statements for unauthorized charges. Be careful about opening attachments or downloading files from e-mail messages; these files may contain viruses or software that can weaken your computer's security.
Forward fraudulent e-mails to the credit union, company, or organization impersonated in the phishing e-mail. If you think you've been a victim of phishing, file a complaint at ftc.gov and then visit the Federal Trade Commission's Identity Theft website at http://www.ftc.gov/bcp/edu/microsites/idtheft/ .
How Phishing works
One way to hook a fish is to use a lure so realistic that the fish thinks it's food. Phishing on the Web works the same way. Thieves send an e-mail or instant message that masquerades--right down to the sender's e-mail address--as a message from a reputable company such as Citibank, eBay or MSN. If you take the bait, you put money--and even your identity--at risk.
The message capitalizes on your trust of a respected brand by enticing you to click a link. Doing so takes you to an equally convincing (and equally fake) Web page or pop-up window that's been set up to imitate the legitimate business. Once there, you're asked to divulge sensitive personal information such as your Social Security number, a bank account or credit card number, or a validation code, password or personal identification number (PIN).
*If you provide the requested information, you may find yourself the victim of identity theft.
From beginning to end, the process involves:
1. Planning. Phishers decide which business to target and determine how to get e-mail addresses for the customers of that business. They often use the same mass-mailing and address collection techniques as spammers.
2. Setup. Once they know which business to spoof and who their victims are, phishers create methods for delivering the message and collecting the data. Most often, this involves e-mail addresses and a web page.
3. Attack. This is the step people are most familiar with -- the phisher sends a phony message that appears to be from a reputable source.
4. Collection. Phishers record the information victims enter into web pages or popup windows.
5. Identity Theft and Fraud. The phishers use the information they've gathered to make illegal purchases or otherwise commit fraud. As many as a fourth of the victims never fully recover
If the phisher wants to coordinate another attack, he evaluates the successes and failures of the completed scam and begins the cycle again.
Technical Trickery
The more complex a web browser or e-mail client is, the more loopholes and weaknesses phishers can find. This means that phishers add to their bags of tricks as programs get more sophisticated. For example, as spam and phishing filters become more effective, phishers get better at sneaking past them.
The most common trick is address spoofing. Many e-mail programs allow users to enter their desired information into the "From" and "Reply-to" fields. While convenient for people who use multiple e-mail address, this makes it easy for phishers to create messages that look like they came from a legitimate source. Some e-mail servers also allow computers to connect to the simple mail transfer protocol (SMTP) port without the use of a password. This allows phishers to connect directly to the e-mail server and instruct it to send messages to victims.
Other tricks include:
Obfuscated links. These URLs look real but direct the victim to the phisher's web site. Some obfuscation techniques include:
Using misspelled versions of the spoofed company's URL or using international domain name (IDN) registration to re-create the target URL using characters from other alphabets.
Including the targeted company's name within an URL that uses another domain name.
Using alternate formats, like hexadecimal, to represent the URL.
Incorporating instructions for redirection into an otherwise legitimate URL.
Using HTML to present links deceptively. For example, the link below looks like it goes to a section of "How Spam Works" that explains zombie machines, but it really directs your browser to an entirely different article on zombies.
Graphics. By determining which e-mail client and browser the victim is using, the phisher can place images of address bars and security padlocks over the real status and address bars.
Popup windows and frames. Malicious popup windows can appear over the site, or invisible frames around it can contain malicious code.
HTML. Some phishing e-mails look like plain text but really include HTML markup containing invisible words and instructions that help the message bypass anti-spam software.
DNS cache poisoning. Also called pharming, this is when a phisher (often by speaking to customer service representatives) changes DNS server information. This causes everyone trying to reach the spoofed company's web site to be directed to another site. Pharming can be hard to detect and can ensnare multiple victims at once.
Phishers can use proxy computers situated between the victim and the site to record victims' transactions. They can also take advantage of poor security at a company's web page and insert malicious code into specific pages. Phishers who use these methods don't have to disguise their links because the victim is at a legitimate Web site when the theft of their information takes place.
Phishers also use malicious programs in their scams:
Key loggers and screen capture Trojans record and report information to the phisher.
Remote access Trojans turn victims' computers into zombies -- machines phishers can use to distribute more phishing e-mail or host phishing web pages.
Bots maintain fabricated conversations with victims in chat rooms or coordinate zombie networks.
Spyware tracks and records users' online behavior, which can help phishers plan other attacks.
You can read more about other techniques used for phishing in Next Generation Security Software's Phishing Guide. Antiphishing.org also has a play-by-play of exactly how one phisher tries to fool his victims.
How to Protect Yourself
Avoid becoming a victim of phishing scams by remembering these helpful tips:
1. Never provide your personal information in response to an unsolicited request, whether it is over the phone or over the Internet. E-mails and Internet pages created by phishers may look exactly like the real thing. They may even have a fake padlock icon that ordinarily is used to denote a secure site. If you did not initiate the communication, you should not provide any information.
2. If you believe the contact may be legitimate, contact the financial institution yourself. You can find phone numbers and Web sites on the monthly statements you receive from your financial institution, or you can look the company up in a phone book or on the Internet. The key is that you should be the one to initiate the contact, using contact information that you have verified yourself.
3. Never provide your password over the phone or in response to an unsolicited Internet request. A financial institution would never ask you to verify your account information online. Thieves armed with this information and your account number can help themselves to your savings.
4. Review account statements regularly to ensure all charges are correct. If your account statement is late in arriving, call your financial institution to find out why. If your financial institution offers electronic account access, periodically review activity online to catch suspicious activity.
Be suspicious of any e-mail with urgent requests for personal financial information unless the e-mail is digitally signed (you can't be sure it wasn't forged or 'spoofed').
Phishers typically: (1) include upsetting or exciting (but false) statements in their e-mail messages to get you to react immediately; (2) ask for confidential information such as usernames, passwords, credit card numbers, social security numbers, account numbers, etc.; and (3) do not personalize the e-mail message (while valid messages from your credit union should be).
Don't use the links in an e-mail to get to any web page if you suspect the message might not be authentic. Instead, call the company on the telephone, or log onto the website directly by typing in the Web address in your browser.
Avoid filling out forms in e-mail messages that ask for personal financial information. You should only communicate information such as credit card numbers or account information via a secure website or the telephone.
Always ensure that you're using a secure website when submitting credit card or other sensitive information via your Web browser. To make sure you're on a secure Web server, check the beginning of the Web address in your browser's address bar - it should be "https://" rather than just "http://".
Consider installing a Web browser tool bar to help protect you from known phishing fraud websites.
Regularly log into your online accounts and don't wait for as long as a month before you check each account.
Regularly check your financial institution, credit, and debit card statements to ensure that all transactions are legitimate. If anything is suspicious, contact your financial institution(s) and card issuers.
Ensure that your browser is up to date and security patches applied.
What to do if you fall victim
What to do if you fall victim:
Contact your financial institution immediately and alert it to the situation.
If you have disclosed sensitive information in a phishing attack, you should also contact one of the three major credit bureaus and discuss whether you need to place a fraud alert on your file, which will help prevent thieves from opening a new account in your name.
Here is the contact information for each bureau's fraud division:
Equifax
800-525-6285
P.O. Box 740250
Atlanta, GA 30374
Experian
888-397-3742
P.O. Box 1017
Allen, TX 75013
TransUnion
800-680-7289
P.O. Box 6790
Fullerton, CA 92634
Report all suspicious contacts to the Federal Trade Commission through the Internet at www.ftc.gov/bcp/edu/microsites/idtheft/, or by calling 1-877-IDTHEFT .
- Forward the e-mail to reportphishing@antiphishing.com;
- Forward the e-mail to the Federal Trade Commission at spam@uce.gov;
- Forward the e-mail to the "abuse" e-mail address at the company that is being spoofed;
- When forwarding spoofed messages, always include the entire original e-mail with its original header information intact; and
- Notify the Internet Fraud Complaint Center of the FBI by filing a complaint on their website: www.ifccfbi.gov/.
Phishing Facts
Phishing Facts:
13,776 phishing attacks linked to 5,259 Web sites took place in August of 2005.
They targeted 84 different businesses, but three businesses received 80 percent of the attacks.
85 percent of the attacks targeted banks and other financial institutions.
Phishers succeed in getting personal information from up to five percent of their intended victims. 57 million U.S. Internet users have received at least one phishing e-mail, and as many as 1.7 million have given personal information to the attackers.
Phishing:
Not Just for E-mail Anymore
E-mail is the most common way to distribute phishing lures, but some scammers seek out victims through:
Instant messages
Cell phone text (SMS) messages
Chat rooms
Fake banner ads
Message boards and mailing lists
Fake job search sites and job offers
Fake browser toolbars
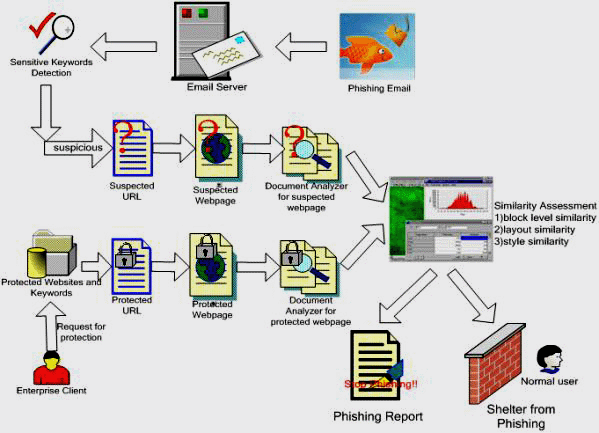
Anti-phishing Work Flow
© by GSO • Contact